For any integration developer, API authentication is the starting line. Think of it as a secure digital handshake—the mandatory first step before a single byte of data can be exchanged between two systems. It’s how an application proves its identity, ensuring that only trusted parties get access to sensitive information. This isn't just a technical hoop to jump through; it's a critical security checkpoint that determines the success and security of your entire integration project.
The Developer's First Hurdle in API Integration
If you're an integration developer building software that connects to other platforms, especially in eCommerce, authentication is the non-negotiable first hurdle. It's like a digital passport control: no valid credentials, no entry. This initial step lays the groundwork for a secure, reliable connection, which is absolutely vital when you're handling sensitive data like customer orders, personal details, or inventory levels.
Getting this right means understanding the different "passports," or authentication methods, that APIs require. The two you’ll run into most often are API Keys and OAuth 2.0. Each has a different purpose and comes with its own set of rules and complexities. Our guide on different API authentication methods offers a deeper look into these mechanisms.
Why Authentication Is So Critical Today
You really can't overstate the importance of solid API authentication. As APIs have become the backbone of modern software, they've also become a prime target for attackers. In 2025 alone, there were over 40,000 API-related security incidents reported, a stark reminder of the risks involved. That surge has made getting security right more important than ever.
For an integration developer, managing authentication isn't just a setup task—it's a continuous responsibility. A single weak point can compromise the entire system, leading to data breaches and loss of trust.
The Challenge for eCommerce Integration Developers
In the world of eCommerce, this problem gets magnified. Every shopping platform—from Shopify to Magento to WooCommerce—seems to have its own unique way of handling authentication. One might use a simple API key, while another demands a complex, multi-step OAuth 2.0 flow that can take days of a developer's time to implement correctly.
This inconsistency creates a huge headache for developers building software that needs to connect to multiple platforms. The typical workflow is a mess:
- Platform-Specific Logic: You end up writing, debugging, and maintaining completely different code to handle the authentication dance for each individual shopping cart.
- Credential Management: You’re forced to build a secure system to store and refresh a growing list of keys, tokens, and secrets for every single store you connect to.
- Ongoing Maintenance: Just when you think you’re done, a platform changes its authentication requirements or deprecates an old method, and it’s back to the drawing board for your team.
This is where a unified API provider like API2Cart completely changes the game. Instead of building and maintaining dozens of separate authentication modules, an integration developer connects to API2Cart just once. It handles the specific authentication logic for over 40 eCommerce platforms behind the scenes, effectively acting as a master key that unlocks them all and dramatically speeds up development time.
Decoding Core API Authentication Methods
For any integration developer, the toolkit for authentication in API connections really boils down to two main methods: API Keys and OAuth 2.0. Getting the fundamental differences, ideal use cases, and the trade-offs between them is the first critical step in building a secure and scalable eCommerce integration. Honestly, the choice you make here sets the foundation for your entire project.
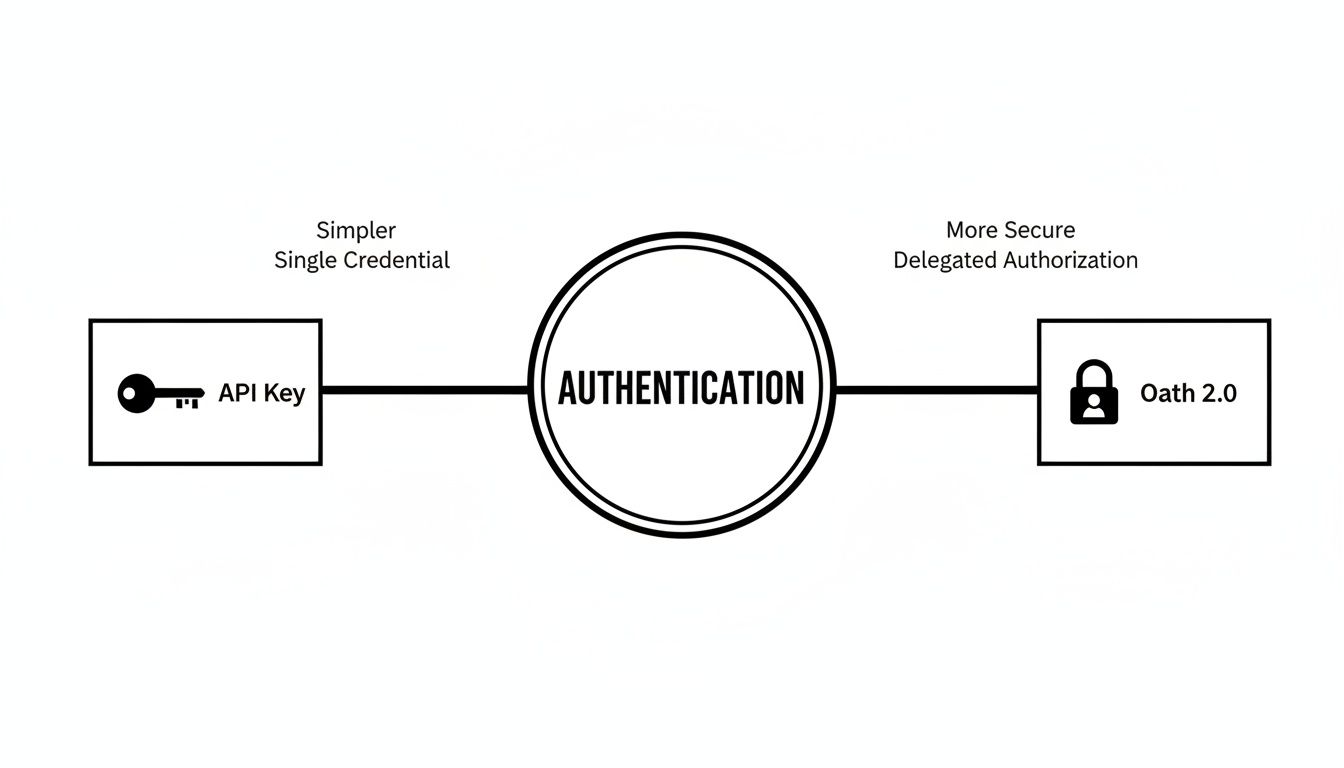
Think of an API Key as the simplest form of authentication you can get—it's like a single, static password for your application. When your software needs to talk to an API, it just presents this key. If it matches what the server expects, access is granted. Simple as that.
This approach is popular because it’s so straightforward to implement. You generate a key, stick it somewhere safe in your application's backend, and include it in your API requests, usually in an HTTP header. It’s a fast way to get an integration off the ground, especially for internal services or basic server-to-server communication where a user isn't directly involved.
The Simplicity and Risk of API Keys
The biggest selling point for API Keys is their ease of use. There's no complicated, multi-step handshake, which makes them appealing for developers who just need to connect services quickly. But this simplicity comes with a pretty significant security price tag.
An API Key is a perpetual key to the kingdom. If it's ever accidentally exposed—say, it gets leaked in client-side code or committed to a public code repository—a malicious actor can use it to gain full access to the associated data until the key is manually revoked.
This "all or nothing" access model is a huge drawback. The key either works and grants full permissions, or it doesn't. There's no middle ground or granular control, making it a poor choice for applications handling sensitive third-party data, which is basically the bread and butter of the eCommerce world.
OAuth 2.0: The Gold Standard for User-Delegated Access
Now, let's pivot to OAuth 2.0, the industry standard for secure, delegated access. If an API Key is a master password, think of OAuth 2.0 as a valet key. It allows a user to grant your application specific, limited permissions to access their data on another service, all without ever sharing their actual username and password with you.
This process involves a multi-step "flow" where the user is sent over to the service they want to connect (like their Shopify store), they log in directly with that service, and then they explicitly approve the permissions your app is requesting.
The upsides to this approach are massive:
- Enhanced Security: Your application never touches the user's main credentials, which dramatically reduces your security liability.
- Granular Permissions (Scopes): You can request specific permissions, known as scopes. For instance, you might only ask for
read_ordersandwrite_products, sticking to the principle of least privilege. - Limited Lifespan: Access is granted through short-lived access tokens. Once they expire, they’re useless. A separate, securely stored refresh token is then used to get a new one, adding another strong layer of security.
If you want to go deeper into how this compares with other token-based systems, we break down the nuances in our article comparing OAuth vs JWT.
To help you decide which method fits your needs, let's break them down side-by-side.
Comparing Common API Authentication Methods
When you're on the hook for building a new integration, choosing the right authentication model is one of the first major technical decisions. The table below gives you a quick snapshot of the key differences to guide that choice.
| Method | Best For | Security Level | Complexity | eCommerce Example |
|---|---|---|---|---|
| API Keys | Server-to-server communication, internal tools, or simple read-only APIs. | Low to Medium | Low | A simple script pulling public product catalog data. |
| OAuth 2.0 | Third-party applications that need to access user data on their behalf. | High | High | A shipping management app that needs to access a merchant's orders and fulfillments in their BigCommerce store. |
While OAuth 2.0 is clearly the more robust and secure option for most eCommerce integrations, that security comes at the cost of development complexity.
The Burden on Integration Developers
While OAuth 2.0 is far more secure, its complexity can be a major headache for developers. Implementing the various flows, managing token expiration and refresh logic, and securely storing credentials for every single connected store is a heavy engineering lift. This is exactly where a unified API provider like API2Cart completely changes the game.
Instead of your team building and maintaining dozens of unique OAuth 2.0 implementations for platforms like Shopify, BigCommerce, and Magento, you integrate with API2Cart just once. API2Cart abstracts away all that complexity. You make a single, standardized call to add a new store, and we handle the entire platform-specific authentication dance on the backend—whether it's OAuth 2.0 or an old-school API key—securely and automatically.
This frees up your team to focus on building valuable product features, not wrestling with complex and ever-changing authentication protocols.
Navigating Real-World Authentication Challenges
Theory is one thing, but as an integration developer, you quickly learn that the real world of eCommerce APIs is a messy, inconsistent landscape. The textbook explanation of authentication in API protocols just doesn't prepare you for the sheer variety you'll encounter out in the wild. This is where development timelines get derailed and complexity skyrockets.
You'll have modern platforms like Shopify using a robust OAuth 2.0 flow, which is great for security but demands a multi-step implementation. At the same time, another major platform might still rely on a single, static API key that offers little in the way of granular control. This forces your team to become experts in multiple authentication schemes, each with its own quirks and pitfalls.
This visual map breaks down the core trade-offs between the two most common approaches you'll face.
The key takeaway here is the classic tug-of-war between the straightforward simplicity of API Keys and the robust, delegated security you get with OAuth 2.0.
The Nightmare of Inconsistent Protocols
For your development team, this isn't just a minor headache; it's a massive development bottleneck. Every new platform you need to integrate with becomes its own separate, resource-draining project.
Suddenly, you're dealing with a unique set of challenges for each connection:
- Custom Code for Every Platform: You're forced to write, test, and deploy bespoke code just to handle the specific authentication logic for every single shopping cart.
- Divergent Error Handling: Each API reports authentication failures differently. This means building custom error-handling logic for everything from expired tokens to invalid credentials and revoked permissions.
- Mounting Security Overhead: You become responsible for securely storing a chaotic mix of long-lived API keys, access tokens, and highly sensitive refresh tokens for every connected store. This dramatically increases your security burden.
All this constant context-switching and duplicated effort grinds progress on your core product to a halt. Instead of building features your customers love, your developers are stuck deciphering authentication docs and debugging credential issues.
The Hidden Complexity of Token Management
Even when platforms use the same standard, like OAuth 2.0, the implementation details can vary wildly. One of the biggest and most persistent pain points for an integration developer is managing the token lifecycle. For security, access tokens are designed to be short-lived, which means you need to build a rock-solid system for refreshing them behind the scenes.
The real challenge isn't just getting that first successful connection; it's the ongoing maintenance. Handling token expiration, securely storing refresh tokens, and gracefully managing revocation without disrupting service is a complex engineering task that has to be solved again for every single integration.
This process involves catching token expiration errors, using a refresh token to request a new access token, and then seamlessly retrying the original API call. Building this logic to be resilient and secure is far from trivial—and once again, it has to be replicated for each platform you support.
How API2Cart Speeds Up Development
This is precisely the integration chaos that a unified API provider like API2Cart was built to solve. Instead of your team wrestling with dozens of different authentication protocols, you integrate just once with API2Cart's standardized API.
Here’s how it cuts through the complexity for an integration developer:
- A Single, Standardized Method: You connect to API2Cart using one consistent authentication process. We handle the unique, often frustrating requirements of over 40 different shopping platforms behind the scenes.
- Automated Token Management: API2Cart manages the entire token lifecycle for you. It automatically handles token refreshes, so your application never has to worry about expired credentials again.
- Reduced Security Burden: We securely store and manage all platform-specific credentials, dramatically reducing your security overhead and compliance risks.
By abstracting away the complexities of authentication in API connections, API2Cart lets your team bypass these common roadblocks entirely. This slashes your time-to-market and frees up your valuable engineering resources to focus on innovation, not repetitive integration plumbing.
How a Unified API Solves Authentication Headaches
After wading through a minefield of inconsistent protocols and tricky token management, the path forward for an integration developer can feel exhausting. The core problem is obvious: building and maintaining dozens of unique authentication modules absolutely drains resources and grinds product development to a halt. This is precisely where a unified API provider steps in, acting like a universal adapter to solve these headaches with one elegant connection.
Instead of hand-coding a solution for Shopify's OAuth 2.0, another for Magento's API keys, and yet another for some platform's bizarre custom scheme, you connect just once. This single integration point becomes your master key, unlocking access to a massive ecosystem of eCommerce platforms without forcing you to learn each one's specific authentication dance.
One Connection to Rule Them All
The biggest win for any integration developer is the sheer drop in complexity. Imagine your app needs to connect to ten different shopping platforms. The old way means ten separate integration projects, each with its own authentication logic, credential storage headaches, and maintenance schedule. A unified API, like API2Cart, collapses all of that into one straightforward task.
You make a single API call to add a new store to your application. That’s it. Behind the scenes, the unified API provider orchestrates the correct, platform-specific authentication flow. Whether it's a complicated, multi-step OAuth 2.0 process or a simple API key exchange, API2Cart handles the entire sequence flawlessly, hiding all the tedious details from you.
For a development team, this means no more parsing through endless, confusing authentication docs for a dozen different platforms. You get to bypass the platform-specific complexities of authentication in API and focus your energy on building features your customers will actually use.
This abstraction layer is incredibly powerful because it translates dozens of complex, wildly different systems into one simple, predictable interaction. Your code stays clean and focused on a single integration, making it way easier to test, maintain, and scale.
Automating the Authentication Lifecycle
A unified API does more than just simplify the first handshake; it manages the entire authentication lifecycle for you. One of the most persistent challenges for developers is handling token expiration and refresh logic—a mission-critical task for keeping the service running without interruptions.
With a solution like API2Cart, this whole process is put on autopilot.
- Initial Connection: When a merchant connects their store, API2Cart securely handles the initial OAuth 2.0 authorization or API key submission.
- Secure Credential Storage: It then stores the necessary credentials, like refresh tokens, in an encrypted vault, taking a significant security burden off your team's shoulders.
- Automatic Token Refresh: Best of all, API2Cart actively monitors access tokens. Before one expires, it automatically uses the stored refresh token to get a new one from the shopping platform. This ensures your API calls never fail because of a stale credential.
The need for secure, automated identity services is exploding. Operator revenue from network APIs globally is forecasted to hit $8 billion by 2030, driven largely by services like Know Your Customer (KYC) APIs that demand rock-solid authentication. You can learn more about this trend from this global market report on secure API connectivity. It’s a clear sign that outsourcing complex authentication to a dedicated provider is the smart move.
The Real-World Impact on Development Speed
By offloading all these responsibilities, a unified API massively accelerates your time-to-market. All those development hours saved from not building and maintaining individual authentication modules can be plowed right back into your core product. For an integration developer, this means you can roll out features faster, expand to new markets quicker, and be far more agile in responding to customer needs.
Ultimately, API2Cart lets your team treat authentication as a solved problem. It provides a single, secure, and reliable gateway to over 40 different shopping platforms, turning what was once a major development bottleneck into a simple, scalable solution.
Implementing Bulletproof API Security Practices
Picking the right authentication in API connections is just the start. The real test is in the implementation—that's what separates a genuinely secure integration from a vulnerable one. As an integration developer, this is where the rubber meets the road. Following security best practices isn’t about checking off a list; it’s about building a foundation of trust and proving you can protect the sensitive data you’re handling.
It's shockingly easy for things to go wrong. One simple mistake, like leaving a token in client-side code, can completely undermine the most advanced authentication setup. The goal is to build defense in layers, so if one part of your security fails, the whole system doesn’t come crashing down.
Mastering the Token Lifecycle
When you're working with protocols like OAuth 2.0, access and refresh tokens are the keys to the kingdom. How you manage their entire lifecycle is probably the most critical part of your integration's security.
First and foremost, treat every token like a password. They should never be stored on the client-side, like in a browser's local storage or a mobile app's files. All tokens need to live on your server, ideally encrypted in a database or locked away in a proper secrets management vault.
You should also keep your access tokens on a short leash. By setting them to expire in 15-60 minutes, you drastically shrink the window an attacker has if a token ever gets stolen. This works because you can use a long-lived (and securely stored) refresh token to quietly grab a new access token in the background, keeping the user's experience smooth while maximizing security. You can find more details in our comprehensive guide on API security best practices.
Adhering to the Principle of Least Privilege
When you kick off an OAuth 2.0 flow, the platform will ask you to request specific permissions, or "scopes." It's tempting to just ask for everything to make development easier down the line, but that's a huge security risk. You need to stick to the principle of least privilege: only ask for the absolute minimum permissions your application needs to do its job.
If your app only needs to read product data, don't ask for permission to write orders. By strictly limiting your requested scopes, you minimize the potential damage if a token is ever compromised.
This isn’t just good for security; it builds trust. A merchant is far more likely to approve an app that requests read-only access for a reporting tool than one that inexplicably asks for full admin rights.
Non-Negotiable Security Layers
Beyond managing tokens, there are a few other security measures that are simply non-negotiable for any modern API integration. Think of these as the baseline for protecting data and warding off common attacks.
- Enforce HTTPS Everywhere: All API traffic must be encrypted with HTTPS (TLS). No exceptions. This prevents attackers from snooping on the connection to steal credentials or other sensitive information.
- Add Multi-Factor Authentication (MFA): Whenever you can, push users to enable MFA on the accounts your integration is accessing. MFA is a powerful defense against account takeovers, even if a user’s password gets compromised. The global MFA market is on track to hit $40 billion by 2030, with adoption already around 70% of users.
- Implement Rate Limiting: You need to protect both your API and the third-party APIs you're hitting. Sensible rate limits on incoming requests can shut down brute-force login attempts and denial-of-service attacks before they cause real damage.
Strong API authentication doesn't exist in a vacuum. It's also critical to secure the servers and services that run your integration. To get the full picture, check out these 10 essential endpoint security best practices.
By layering these practices together, you create a tough, resilient security posture that protects your app, your users, and their data from whatever threats come next.
Your Path to Seamless and Secure Integration
If you’re an integration developer, you already know the headache of connecting to different eCommerce platforms. The world of authentication in API connections is a tangled mess of modern OAuth 2.0 flows and older, clunky API key systems. Each one needs its own unique code and special care. Getting a handle on the pros and cons of each is just the first step.
The real problem, though, is the sheer amount of development time these inconsistencies eat up. Building, testing, and maintaining separate authentication modules for dozens of platforms isn't just inefficient—it actively slows down innovation. This is exactly where a unified API provider can give you a massive strategic advantage.
Speed Up with a Unified Solution
Instead of fighting with every single protocol, you can use a service like API2Cart to handle all that complexity for you. This approach doesn't just speed up development; it also lifts a huge security burden off your shoulders.
Think about what this means for your day-to-day work as an integration developer:
- Rapid Onboarding: Imagine connecting a new merchant's store in minutes with just one, standardized API call. API2Cart takes care of the platform-specific OAuth handshake or key exchange behind the scenes.
- Zero-Maintenance Authentication: Forget about building complicated token refresh logic. API2Cart automatically manages the entire token lifecycle, making sure your integration stays connected without any interruptions from expired credentials.
- Focus on Core Features: When you offload authentication, your engineering team can stop worrying about managing credentials and get back to what they do best: building valuable features for your customers, like advanced order management or inventory synchronization.
The goal isn't to become an expert in dozens of proprietary authentication schemes; it's to solve customer problems. Shifting your focus from wrestling with protocols to creating business value is the key. Modern tools like a unified API let you build scalable, secure, and resilient eCommerce integrations in a fraction of the time. By outsourcing this complexity, you get to that goal much faster.
Frequently Asked Questions
When you're dealing with API connections in the wild, especially across the sprawling eCommerce world, a few questions always pop up. Here are some of the most common ones we hear from integration developers, with straightforward answers.
What Is the Main Difference Between an API Key and OAuth 2.0?
The biggest difference for an integration developer boils down to control and scope. Think of an API Key as a static secret, like a master key to your application. If someone gets their hands on it, they have full access until you manually revoke it. We’ve all seen the security horror stories where a single leaked key leads to a massive data breach.
OAuth 2.0, on the other hand, provides delegated, temporary access. A user grants your app permission to do specific things on their behalf (these are the "scopes"), and your app gets a short-lived access token. It's a much safer approach because you never touch the user's actual login details, and the access you have is both limited and revocable.
How Does API2Cart Handle Authentication Token Expiration?
This is one of those critical but tedious tasks that API2Cart handles for you completely, saving your team a ton of headaches. For protocols like OAuth 2.0, API2Cart securely stores the refresh token right after the user establishes the initial connection.
From there, it keeps an eye on the access token's validity. Just before it expires, API2Cart automatically uses the refresh token to get a new one from the shopping platform. This entire cycle happens behind the scenes, so your application's API calls continue to work without a hitch. You never have to worry about a call failing due to an expired token or building out your own complex refresh logic.
Why Are Scopes in OAuth 2.0 Important for eCommerce?
Scopes are absolutely vital for security because they enforce what's known as the principle of least privilege. Instead of asking for the keys to the entire kingdom (a merchant's store), your integration requests only the specific permissions it truly needs, like 'read_products' or 'write_orders'.
This means if your app's access token were ever compromised, the potential damage is strictly limited to only those authorized actions. For store owners, this provides crucial peace of mind, and for developers, it significantly reduces the security liability of the integration.
This kind of granular control is a cornerstone of any trustworthy, modern application.
Can I Still Use API Keys Through API2Cart?
Yes, absolutely. While OAuth 2.0 is the modern standard, plenty of eCommerce platforms still run on static API keys. When you add a store that uses this method, API2Cart gives you a standardized and secure way to submit and store those credentials.
The real benefit for an integration developer is that your application doesn't have to care about the difference. You use the exact same process to add any store, and API2Cart figures out whether to handle an OAuth 2.0 flow or manage an API key in the background. This unified approach is a massive accelerator for development and makes maintenance a breeze.
Ready to stop wrestling with dozens of authentication protocols and accelerate your time-to-market? With API2Cart, you can connect to over 40 shopping platforms using a single, unified API. Start your free 14-day trial today!