It's easy to get tangled in the OAuth vs. JWT debate, but here’s the most important thing to remember: they aren't competitors. The real difference is their role. OAuth is an authorization framework—a set of rules for granting access—while JWT is a token format, a standard for securely sending information.
They are often used together, where a standard OAuth flow issues an access token that happens to be formatted as a JWT. For any integration developer building secure APIs, nailing this distinction is the first and most critical step.
Unpacking the Core Difference for Integration Developers
If you're an integration developer, thinking in terms of "OAuth vs. JWT" is a red herring. It's like comparing the rules of mail delivery to the physical design of an envelope. You need both to get a message delivered safely. OAuth 2.0 is the standardized process that lets a user grant your app permission to access their data on another service, all without you ever seeing their password.
A JWT (JSON Web Token), on the other hand, is just a compact, self-contained way to represent claims between two parties. When an OAuth server grants your application an access token, that token is very often structured as a JWT. It’s the "envelope," holding claims about the user and their permissions, all cryptographically signed so you know it hasn't been opened or altered in transit.
This distinction becomes incredibly important when you're connecting to multiple APIs, especially in the eCommerce world. Each platform—think Shopify, BigCommerce, or Magento—might use a slightly different flavor of OAuth or have unique rules for managing tokens. Trying to build and maintain these connections one by one eats up a massive amount of engineering time.
For a B2B SaaS vendor, the real challenge isn't just understanding OAuth vs JWT, but implementing and managing dozens of unique authentication flows at scale. The complexity multiplies with each new platform integration.
This is exactly where a unified integration platform like API2Cart comes in. Instead of wrestling with the authentication specifics for over 60 different eCommerce platforms, your team can connect to a single, consistent API. API2Cart handles all the underlying OAuth flows and other authentication mechanisms, completely abstracting away the complexity. This frees up your developers to build core features for your app, not become experts on every platform's token quirks, which dramatically accelerates your integration roadmap. To get a broader view on this topic, you can explore our guide on the fundamentals of API access.
OAuth 2.0 Framework vs JWT Token Format at a Glance
To put it simply, one is a process, and the other is a payload. This table breaks down the fundamental differences between the OAuth 2.0 framework and the JWT token format, highlighting their distinct roles for an integration developer.
| Aspect | OAuth 2.0 | JWT (JSON Web Token) |
|---|---|---|
| Primary Role | An authorization framework that defines processes for securely delegating access. | A token format used to securely transmit information (claims) between parties. |
| Main Purpose | To grant a third-party application limited access to a user's resources without exposing credentials. | To represent claims in a compact and self-contained way, verifiable via a digital signature. |
| Typical Use Case | Enabling "Login with Google," connecting a SaaS app to a user's eCommerce store, or authorizing API access. | Acting as the access token in an OAuth flow or for stateless authentication between microservices. |
| Relationship | A process. OAuth defines the "how"—the steps for obtaining an access token. | A payload. JWT can be the "what"—the actual access token issued by an OAuth server. |
Ultimately, understanding that OAuth is the "how" and JWT is the "what" clarifies their relationship and helps you make better architectural decisions for your integrations.
How OAuth 2.0 Manages Delegated Authorization
At its heart, OAuth 2.0 is the industry standard for delegated authorization. Think of it as a secure valet key for your data. It lets a third-party application access a user's information on their behalf without ever touching their password. For any integration developer, understanding this flow is non-negotiable—it's the handshake that connects your app to other services.
The whole process revolves around a clean separation of roles. This isn't just for show; it's a security-first design that ensures access is only granted with explicit, informed user consent. Every player in this dance has a specific job to do.
The Key Roles in Any OAuth Flow
When you break it down, every OAuth 2.0 flow involves four main actors working together to grant access to protected resources securely.
- Resource Owner: This is simply the end-user. They own the data and are the only ones who can approve access to it. A perfect example is a merchant who wants to connect their Shopify store to your inventory management SaaS.
- Client: This is your application. It’s the one requesting access to the Resource Owner's data.
- Authorization Server: This is the gatekeeper. It’s responsible for verifying the user's identity, getting their consent, and ultimately issuing the access token your app needs.
- Resource Server: This is the API where the user's data actually lives. It's the final stop, validating the access token before handing over the requested information.
This structured model is brilliant because it means your application never has to store or even see the user's login credentials. That alone dramatically slashes your security risks.
Understanding Common Grant Types
OAuth isn't a one-size-fits-all protocol. It defines several "grant types," which are just different methods for getting an access token. The one you use depends entirely on your application's architecture and the integration scenario you're building for.
The Authorization Code grant is by far the most common and secure flow for web and mobile apps where a user is actively involved. The user gets redirected to the Authorization Server (like a "Log in with Google" screen), approves the request, and the server sends a temporary authorization code back to your app. You then trade that code for an actual access token behind the scenes.
On the other hand, the Client Credentials grant is built for machine-to-machine communication where no user is present. In this flow, your application authenticates itself directly with the Authorization Server to get a token for accessing its own resources, not a user's. Choosing the right flow is a critical first step, and you can learn more about selecting the appropriate OAuth type for your API in our detailed guide.
The real challenge for B2B SaaS developers isn't just knowing one OAuth flow, but mastering dozens. Each eCommerce platform like Shopify, Magento, or BigCommerce can have subtle yet critical differences in its implementation, turning integration into a complex, time-consuming task.
This is where a unified API solution becomes a massive accelerator. Instead of building and maintaining separate OAuth flows for over 60 different shopping carts, a platform like API2Cart handles this complexity for you. It abstracts away the unique authentication and authorization quirks of each platform, giving you a single, consistent integration point. Your dev team gets to focus on building features, not wrestling with token exchanges, which radically shortens your time-to-market. This kind of efficiency is becoming mission-critical as the API Management Market is projected to grow at a CAGR of 21.49% through 2033, largely driven by the need to manage standards like OAuth and JWT.
Deconstructing JWT: A Guide to the Token Format
While OAuth 2.0 lays out the rules for the authorization dance, a JSON Web Token (JWT) is often the key that gets handed over at the end. For any integration developer, knowing what's inside that key is non-negotiable. Think of a JWT as a compact, self-contained digital envelope designed to securely pass information as a JSON object.
Its real superpower is being self-contained. Everything the receiving service needs to verify a request is packed right into the token itself. This means you can skip hitting the database to check permissions on every single API call—a stateless approach that's foundational for building scalable, high-performance systems.
The Three Parts of a JWT
Every JWT you see will have three distinct parts, separated by dots (.), creating that familiar xxxxx.yyyyy.zzzzz structure. Each piece is Base64Url encoded.
- Header: The first part is simple. It typically contains two bits of info: the token type (
typ), which is always "JWT," and the signing algorithm being used (alg), likeHS256orRS256. It’s basically the instruction manual for how the token’s signature was created. - Payload: This is the core of the token. It holds the "claims"—statements about an entity (usually a user) plus some handy metadata. This is where you'll find standard details like the token issuer (
iss), the subject (sub), and, critically, the expiration time (exp). - Signature: To create the signature, you take the encoded header and payload, combine them with a secret key, and run it all through the algorithm specified in the header. This signature is what proves the sender is who they say they are and guarantees the token hasn't been messed with in transit.
If you want to go deeper on this, there’s a great resource that breaks down what JWTs are and how secure they are, which is a perfect supplement to this overview.
The Payload and Its Critical Role for Developers
For integration developers, the payload is where the magic happens. It’s not just for standard claims; it’s a flexible space where you can embed custom data that your application needs to make smart authorization decisions on the fly.
For instance, when you're integrating with dozens of eCommerce platforms, a JWT payload might include custom claims like a store_id to specify which merchant account the user can access, or a list of permissions such as "read:orders" and "write:products". When your API gets a token like this, it can validate the signature instantly and then use those claims to grant or deny access without a single database lookup.
The real power of JWTs for integration developers lies in the payload's custom claims. They allow you to build stateless authorization systems that are both fast and granular, which is essential when managing permissions across dozens of different connected systems.
This kind of efficiency is a game-changer in the B2B eCommerce SaaS world. Imagine your platform is connected to thousands of merchant stores. If you had to query a database to check permissions for every single API call, you’d create a massive performance bottleneck.
This is exactly the kind of headache a unified API platform like API2Cart is built to solve. By handling the authentication and token management across more than 60 eCommerce platforms, API2Cart abstracts away the complexity. You just interact with a consistent API, and the necessary permissions and store contexts are handled for you, letting you focus on your application's core logic instead of getting bogged down in decoding countless token variations.
When you move past the definitions, the real OAuth vs. JWT debate for developers happens at the implementation level. Key architectural decisions about state, token revocation, and security dependencies create some major tradeoffs. Getting these differences right is absolutely critical for building a secure and scalable integration.
A huge distinction comes down to state management. JWTs are designed from the ground up to be stateless. The token itself carries all the information a resource server needs to validate a request—user identity, permissions, expiration date, you name it. This self-contained approach means your API doesn't have to hit a database to verify the token, which can be a massive performance win, especially in distributed or microservices setups.
On the other hand, an OAuth flow can use either stateless JWTs or stateful opaque tokens. An opaque token is just a random string that points to session information stored on the authorization server. While this adds a database lookup for validation (and thus, state), it gives you a major security advantage that stateless JWTs simply can't offer by design.
The Challenge of Token Revocation
The most critical security tradeoff for an integration developer is token revocation. What do you do when a token is compromised, or a user's permissions need to change right now?
With a stateful, opaque token, revocation is easy. You just delete the session data on the server tied to that token. The next time the token shows up, the lookup fails, and access is denied instantly. It gives you immediate and guaranteed control.
Revoking a stateless JWT, however, is notoriously difficult. Because the token is self-contained and validated by its cryptographic signature, it remains valid until its expiration time (exp claim), no matter what happens on your server. There's no central "off switch" for a compromised JWT.
The inability to immediately revoke a stateless JWT is its single greatest security weakness. Once issued, a valid JWT is a golden ticket that works everywhere until it expires. This makes short token lifespans an absolute necessity.
To handle this risk, a common best practice is to issue JWTs with very short lifespans—think 5 to 15 minutes. This drastically limits the window of opportunity for an attacker if a token is stolen. When the short-lived JWT expires, the client application uses a long-lived refresh token (a core part of the OAuth flow) to securely get a new one. This keeps the user experience smooth while minimizing risk. Building a solid strategy around this is a core part of your API security best practices.
Security Dependencies and Architectural Impact
The security model for each also looks quite different. A JWT's security hangs entirely on the secrecy of its signing key. If an attacker gets that key, they can forge valid tokens for any user with any permissions they want, completely wrecking your system. This makes disciplined key management, including regular rotation and secure storage, non-negotiable.
OAuth, as a full framework, distributes security responsibilities. It defines secure protocols for getting tokens, validating client identities, and handling user consent, which reduces the chance of credentials being exposed in the first place. The security is baked into the entire process, not just the final token.
This table breaks down the core technical and security differences that developers need to weigh when choosing between these technologies for their API integrations.
Technical Comparison of OAuth 2.0 and JWT
| Feature | OAuth 2.0 (Framework) | JWT (Token Format) | Developer Insight |
|---|---|---|---|
| Primary Role | An authorization framework that defines flows for granting access to resources. It's about delegation. | A token format standard for securely transmitting information as a JSON object. It's about information exchange. | Think of it this way: OAuth is the recipe for getting a key, while a JWT is one possible type of key you can get. They are not mutually exclusive; they're often used together. |
| State Management | Can be stateful (using opaque reference tokens) or stateless (by issuing JWTs as access tokens). | Inherently stateless. The token is self-contained with claims, signature, and expiration. | Stateless JWTs are great for performance in microservices, but stateful tokens give you instant, server-side control over sessions, which is a massive security win. |
| Token Revocation | Easy with stateful tokens (delete the server-side session). Difficult if using stateless JWTs. | Very difficult by design. A JWT is valid until it expires. Workarounds exist but add complexity. | This is the biggest tradeoff. If you need to kill a session immediately (e.g., user logs out, password change), a stateful OAuth token is your best bet. With JWTs, you must rely on short expiry times. |
| Security Model | Relies on a secure, multi-step flow involving the client, user, and authorization server. Manages consent. | Relies on the secrecy of the signing key (for JWS) or encryption key (for JWE). | An OAuth flow protects the token issuance process. A JWT's security is all about protecting that one secret key. If the key leaks, your entire system is compromised until you rotate it. |
| Common Use Case | Third-party authorization ("Log in with Google"), protecting APIs where users delegate access to applications. | Representing user identity and permissions within an API call, securing communication between microservices. | Use OAuth when you need to let an application act on behalf of a user. Use JWTs when you need to pass verifiable identity information between two trusted parties. |
| Implementation | More complex. Requires managing different grant types (Authorization Code, Client Credentials, etc.) and redirects. | Simpler to generate and validate once you have a library. The complexity lies in managing keys and claims. | OAuth setup has a higher initial learning curve, but libraries exist for every language. JWTs are easier to start with but demand rigorous key management and a solid refresh token strategy. |
Ultimately, the best approach for modern APIs isn't choosing one over the other, but using them together. An OAuth 2.0 flow is the gold standard for securely issuing tokens, and JWT is an excellent format for those tokens because it’s compact and stateless.
This layered approach is reflected across the global authentication solutions market. Major players like Microsoft and Okta, holding a combined 42% market share, heavily invest in frameworks that often combine OAuth flows with JWT tokens to get the best of both worlds. The Multi-Factor Authentication (MFA) segment, which dominates with a 60% share, frequently uses these combined technologies for stronger protection.
Beyond the specific tech, both OAuth and JWT are foundational pieces of an organization's overall cybersecurity risk management strategy. For an integration developer, the choice isn't just about performance but about building a resilient, secure system. This is where API2Cart adds immense value. Instead of wrestling with complex key rotation schedules, refresh token logic, and diverse revocation strategies for dozens of eCommerce platforms, you can rely on a single, secure integration point. API2Cart handles these critical security tradeoffs on your behalf, letting your team focus on building features, not a complex web of authentication protocols.
Choosing Your Integration Strategy
Deciding between OAuth and JWT isn't just a technical preference; it's a fundamental architectural choice that hinges on your specific use case. For any integration developer, getting this right from the start means preventing costly refactoring and closing potential security holes down the road.
The decision really comes down to the context of the interaction. Are you trying to give a third-party application limited access to user data? Or are you securing communication between your own internal services? Each scenario has a clear, technically superior approach that finds the right balance between security, performance, and user experience.
Common Integration Scenarios
The best way for an integration developer to pick a path is to map their needs to established industry patterns. Here are three common scenarios and the recommended strategy for each.
- Securing Internal Microservices: When services inside your own trusted network need to talk to each other, speed is everything. In this case, using JWTs alone is often the smartest move. One service authenticates, gets a JWT, and then passes it along to other internal services. Each service can validate the token statelessly without calling a central authorization server, which keeps latency to a minimum.
- Enabling Third-Party Application Access: This is the classic textbook case for the full OAuth 2.0 framework. If you need to let an external app (like a B2B SaaS tool) access a user's data on your platform without them ever sharing their password, OAuth is the non-negotiable standard. It handles the consent screens, secure token issuance, and refresh token logic needed for safe, delegated access.
- Building a Single-Page Application (SPA): For modern web apps, the most secure and robust pattern is actually a combination of both. You use an OAuth 2.0 flow (specifically the Authorization Code flow with PKCE) to manage the user login and consent process. The authorization server then issues a short-lived JWT as the access token, which the SPA can send to your backend APIs with every request.
The optimal strategy is rarely "OAuth vs JWT" but rather "OAuth with JWT." This combination gives you the secure, standardized delegation of OAuth and the stateless, portable efficiency of JWTs, creating a powerful solution for most modern applications.
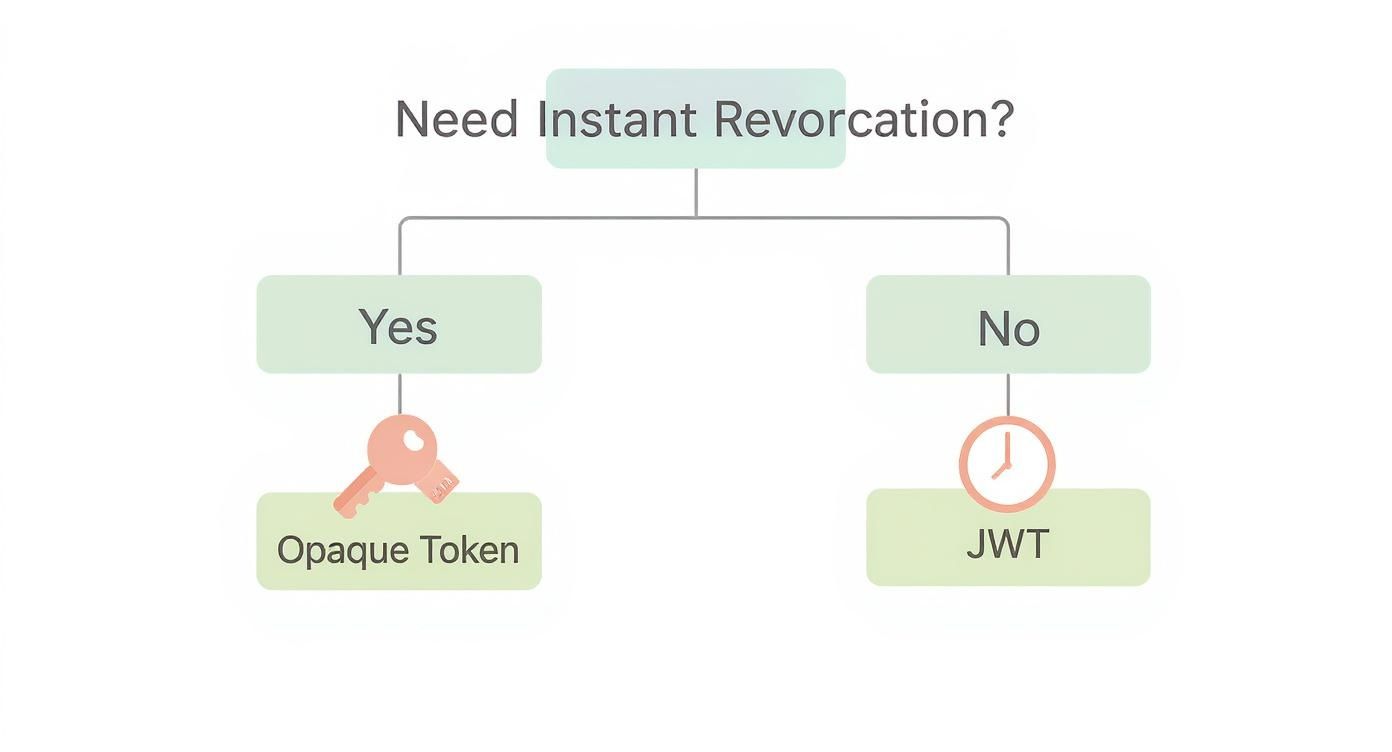
This decision tree helps visualize the critical choice between an opaque token and a JWT, which often comes down to whether you need the ability to revoke access instantly.
As the chart shows, if your application absolutely must be able to revoke a user's access at a moment's notice, a stateful, opaque token is the way to go.
For B2B eCommerce developers, these decisions get even more complicated because you have to deal with dozens of different platforms. This is where a unified API like API2Cart comes in. It abstracts away all the underlying authentication complexity. Instead of building and maintaining unique OAuth flows for over 60 different shopping carts, you integrate just once. API2Cart handles all the diverse authentication strategies behind the scenes, dramatically speeding up your development cycle.
How API2Cart Speeds Up eCommerce Integrations
For any integration developer working in B2B eCommerce, the whole OAuth vs. JWT debate can feel a bit academic. The real nightmare isn't understanding the standards; it's building and maintaining dozens of unique authentication flows for platforms like Shopify, Magento, WooCommerce, and BigCommerce. Each one has its own quirks for handling OAuth, token lifecycles, and credential management.
This fragmentation means development teams burn a shocking amount of time just on authentication. Connecting to each platform one by one is slow, expensive, and pulls your best engineers away from your application's core features. It builds up a massive technical debt that only gets worse with every new platform you decide to support.
Cutting Through the Authentication Noise
Instead of getting bogged down in the different authentication protocols of over 60 shopping carts and marketplaces, a unified integration platform gives you a much smarter path forward. API2Cart was built to solve this exact problem, acting as an abstraction layer between your app and the entire eCommerce ecosystem.
You integrate just once with the API2Cart unified API, and it takes care of all the tricky authentication handshakes for you. That includes managing different OAuth grant types, handling all the refresh token logic, and normalizing the data you get back.
This screenshot from the API2Cart homepage gets right to the point, showing its core value for developers who need to connect with multiple eCommerce platforms.
The visual clearly shows how you can connect to dozens of platforms through one API, which is the perfect solution for the integration mess we've been talking about.
By abstracting away the underlying authentication complexity, API2Cart transforms a multi-faceted integration problem into a single, manageable connection. This allows developers to focus on application logic instead of becoming experts on dozens of different token management systems.
This approach massively accelerates your time-to-market and slashes the ongoing maintenance burden. Your team can add support for a new shopping platform without writing a single new line of authentication code—a huge competitive advantage.
A Practical Solution for Scaling Your Business
The demand for solid, standardized authentication is blowing up everywhere. Take the asset tokenization market, for example, which is valued at $1.244 trillion in 2025. It leans heavily on OAuth and JWT to secure digital asset transactions. The tokenization platforms making up 59.60% of that market's revenue rely on these protocols to manage authorization and secure token exchanges, which shows just how vital this tech is for modern systems. You can find more details in these trends in asset tokenization statistics.
Just like middleware simplifies things in finance, API2Cart provides the must-have infrastructure for eCommerce integrations. Instead of spending weeks setting up a new connection, your developers can add a new store and start syncing data in minutes. This lets you scale your business by easily expanding your reach to over one million potential merchants.
By using API2Cart, you can:
- Slash Development Time: Stop building and maintaining individual authentication flows for every shopping platform.
- Lower Integration Costs: Save on engineering resources and get rid of the long-term costs of patching and updating dozens of connectors.
- Sharpen Your Focus: Let your team concentrate on building cool features for your customers, not on integration plumbing.
At the end of the day, API2Cart offers a practical, scalable way to sidestep the whole OAuth vs. JWT headache at the implementation level, helping you deliver faster, more reliable eCommerce integrations.
Frequently Asked Questions About OAuth and JWT
Even after you get the hang of OAuth vs. JWT, some common questions always pop up during implementation. These two technologies work together, but their specific roles can cause a lot of confusion. Getting these details right from the start is the key to avoiding architectural headaches down the road.
For B2B SaaS developers, the stakes are even higher. A simple misunderstanding about refresh tokens or when to use an opaque token can snowball into a security mess or a clunky user experience—problems that get much worse when you're integrating with dozens of different eCommerce platforms.
Can I Use JWT for Authentication Without OAuth?
Absolutely. This is a very common pattern, especially for your own applications. Once a user logs in with a username and password, your server can generate a signed JWT and send it back. The client app then just includes that JWT in the Authorization header for every API request it makes.
It’s a clean, stateless way to secure communication between a frontend and backend you control. But that’s where it stops. This setup has none of the standardized protocols for third-party delegated access that OAuth was built for. It’s a solution for internal authentication, not for letting another application access your user’s data on their behalf.
Is OAuth More Secure Than Using JWTs Alone?
This is a bit like asking if a blueprint is more secure than a door lock. They solve different parts of the same problem. OAuth is a complete authorization framework. It defines the entire process for granting access securely, managing user consent, and making sure credentials are never exposed to the wrong parties. That makes it inherently more robust for any scenario involving third-party apps.
A JWT, on the other hand, is just a token format. Its security is all about how you implement it—using strong signing keys, validating its claims correctly, and always sending it over HTTPS. An OAuth flow gives you a secure process, while a JWT gives you a secure payload that’s often used within that process.
OAuth provides the secure rulebook for how to get and manage access, while a JWT provides a verifiable container for the permissions granted during that process. One is the procedure, the other is the proof.
What Is the Role of a Refresh Token with JWTs?
When you use JWTs as access tokens inside an OAuth flow, you should make them extremely short-lived—think 5-15 minutes. This drastically limits the damage if a token is ever leaked. So, how do you keep users logged in? That’s where the Refresh Token comes in. It’s a separate, long-lived credential issued at the same time as the short-lived JWT.
Once the access token (the JWT) expires, the client sends the refresh token back to the authorization server. If the refresh token is still valid, the server issues a brand-new, short-lived JWT. This whole dance provides a great user experience by avoiding constant logins, all while keeping the powerful access tokens on a very short leash. Juggling this logic across 60+ platforms is a huge pain, and it’s one of the core complexities API2Cart handles for you.
When Is an Opaque Token Better Than a JWT?
An opaque token is just a random string of characters. Unlike a JWT, which contains user data, an opaque token is just a pointer to session information stored on your server. It’s completely meaningless on its own.
This design gives opaque tokens a massive advantage in one specific area: immediate and guaranteed token revocation. If you need to kick a user out right now, you just delete their session data from your server, and the token is instantly useless. This makes them the go-to choice for high-security situations where you need absolute control over session termination. The tradeoff, of course, is that they are stateful. Every single API request requires a database lookup to validate the token, which can create performance bottlenecks at scale.
Managing these authentication nuances across dozens of platforms is a massive undertaking. Instead of wrestling with token lifecycles and diverse security models, let API2Cart handle it for you. Our unified API abstracts away the complexity of connecting to over 60 eCommerce platforms, allowing you to focus on your core product and accelerate your time-to-market. Explore API2Cart and simplify your integrations today.