Originally, OAuth type was introduced to replace basic authentication, where usernames and passwords were sent with every request.
As a result, once credentials were compromised, attackers gained full access to API data and systems.
Today, API traffic makes up around
83% of all web traffic
, highlighting how broadly APIs are used and how critical secure authorization has become.
At the same time, OAuth 2.0 adoption has grown significantly: it is now used by nearly 16,000 companies across 105 countries as a primary API authentication method,
establishing it as the dominant standard for delegated authorization and API access control.
What Is OAuth 1.0 and How Does This OAuth Type Work?
In general, OAuth 1.0 (defined in RFC 5849 ) is considered a more secure OAuth type. However, it is also less flexible and more complex than OAuth 2.0.
At its core, OAuth 1.0 relies on shared secrets between the client and the server. As a result, every API request includes a cryptographic signature. This signature allows the server to verify the request’s authenticity.
Compared to other OAuth types, OAuth 1.0 introduces additional authorization steps. First, the client requests a temporary request token from the server. Then, this token is exchanged for an access token, similar to the authorization code in OAuth 2.0.
One key advantage of OAuth 1.0 is that token secrets are never transmitted directly. Therefore, sensitive credentials never travel over the network in plain form. Moreover, this OAuth type can work without SSL, although HTTPS is still recommended for sensitive data.
At the same time, OAuth 1.0 requires extra effort from developers. You must generate and validate request signatures using specific hashing algorithms. Fortunately, most modern programming languages provide libraries that simplify this process.
What Is OAuth 2.0 and Why Is This OAuth Type So Popular?
OAuth 2.0 is a widely used OAuth type that simplifies authorization by removing request signatures. Instead, it relies on HTTPS (SSL/TLS) to protect access tokens during transmission.
Because of this approach, OAuth 2.0 is easier to implement for third-party applications. As a result, many platforms adopt it to speed up integration and reduce development complexity.
However, this OAuth type requires careful HTTPS configuration. For example, incorrect certificate validation or token handling can weaken security. Despite these risks, OAuth 2.0 remains the default choice for most modern APIs.
Another important advantage is flexibility. OAuth 2.0 allows users to define scopes. Therefore, applications can access only specific actions or data. This limits what third parties can do with user information.
In short, OAuth 2.0 trades some cryptographic complexity for usability and scalability. That is why it is commonly used across SaaS and eCommerce platforms.
See the OAuth 2.0 flow below.
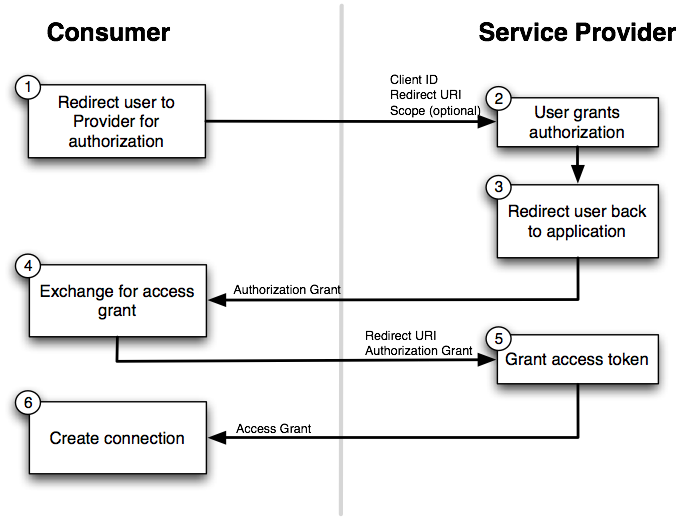
Both OAuth 1.0 and OAuth 2.0 are good in their own way. The inference is it is only you who can decide which is better for you.
In Practice: Accessing Store Data via API2Cart
Once the OAuth 2.0 authorization flow is completed, your application receives an access token. After that, it can securely request store data without handling platform-specific authentication logic. In practice, this is where API2Cart simplifies the workflow.
For example, after a Shopify store is connected via OAuth 2.0, you can retrieve product data using a single, unified API call. Below is the ProductList method for Shopify , which works only after successful OAuth authorization.
This method returns a standardized response, regardless of the underlying eCommerce platform. As a result, your SaaS does not need to adapt to Shopify-specific OAuth nuances or data formats.
Response Structure: ProductList Method (after OAuth 2.0)
{
"return_code": 0,
"return_message": "OK",
"pagination": {
"previous": null,
"next": null
},
"result": {
"products_count": 1,
"product": [
{
"id": "123456",
"name": "Sample Product",
"price": 29.99,
"quantity": 15,
"in_stock": true,
"sku": "SKU-001"
}
]
}
}
In other words, OAuth 2.0 handles secure access, while API2Cart normalizes the data layer. This combination allows SaaS teams to focus on business logic instead of authentication edge cases and platform-specific API differences.
Conclusion: Choosing the Right OAuth Type for Your SaaS
Both OAuth 1.0 and OAuth 2.0 are valid OAuth types. However, OAuth 2.0 is usually the practical choice for scalable SaaS integrations.
If your product integrates with multiple eCommerce platforms, managing OAuth flows in-house quickly becomes expensive and error-prone. In this case, a unified integration layer makes a real difference.
Start a free trial and see how API2Cart simplifies OAuth-based integrations across 60+ platforms.
FAQs
What is the main difference between OAuth 1.0 and OAuth 2.0?
The key difference lies in how security is handled. OAuth 1.0 relies on cryptographic request signatures and shared secrets, meaning credentials are never sent directly over the network. In contrast, OAuth 2.0 removes request signatures and instead depends on HTTPS to protect access tokens, which significantly simplifies implementation.
As a result, OAuth 1.0 offers stronger built-in cryptographic protection, while OAuth 2.0 prioritizes flexibility, scalability, and ease of integration for modern APIs.
Why is OAuth 2.0 the dominant OAuth type for modern APIs?
OAuth 2.0 is widely adopted because it reduces implementation complexity and speeds up third-party integrations. By leveraging HTTPS instead of request signatures, developers can integrate APIs faster and with fewer authentication steps.
Moreover, OAuth 2.0 supports scopes, allowing applications to request limited access to user data. This makes it especially suitable for SaaS and eCommerce platforms that need controlled, scalable authorization.
What challenges do SaaS teams face when managing OAuth flows across multiple platforms?
Managing OAuth in-house becomes complex when working with multiple platforms, each with its own authorization nuances, token lifetimes, and refresh logic. Over time, this increases maintenance costs and raises the risk of security misconfigurations.
Therefore, many SaaS teams look for ways to abstract OAuth handling, so they can focus on business logic instead of continuously adapting to platform-specific authentication changes.
How does API2Cart simplify OAuth 2.0–based integrations?
API2Cart handles OAuth 2.0 authorization at the platform level and provides your application with unified access to store data after authorization is complete. Once a store is connected, your SaaS can retrieve products, orders, customers, and inventory through standardized API methods.
Consequently, you avoid implementing and maintaining separate OAuth flows for each platform while working with normalized data across 60+ eCommerce platforms.