API security has always been a thing of high priority though not always regarded this way by many developer teams. Testing is essential, but sometimes it is not enough. Remember “Criminal Minds”? To catch a criminal, you have to think like one. The same can be applied here, you have to think like a hacker to figure out what kinds of attacks they might try and then try them yourself.
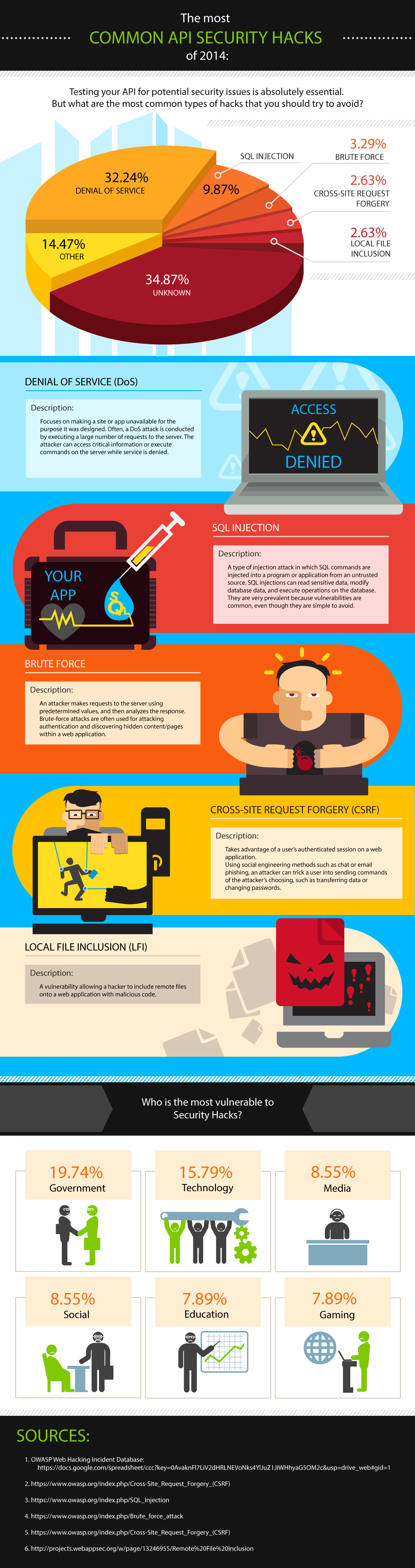
Web Hacking Incident Database (WHID) has done some of the work for you and gathered not only a comprehensive knowledge of web application security, but also statistics of real-world web hacking incidents with summaries included. According to it, top attack methods (and their count at the time of the table being compiled) are:
- unknown (451) (what do you think they could be?)
- denial of service (272)
- SQL injection (233)
- cross site scripting (XSS) (80)
- brute force (47)
- predictable resource location (37)
- stolen credentials (36)
- banking trojan (27)
- unintentional information disclosure (27)
- credential / session prediction (19)
Now that you know what methods to test API security with, take a look at the infographic made by SmartBear Software to see the most common security hacks of the year 2014 explained. There you will also find some information about what institutions are the most vulnerable.
If you have questions regarding the work of API2Cart and how it can be useful for a developer, do not hesitate to schedule a FREE consultation with our representative.